Reading junk spam messages isn’t exactly my idea of a good time, but sometimes fun can be had when you take a moment to check who really sent the email. Here’s the simple story of how a recent spam email advertising celebrity “diet pills” was traced back to a Washington, D.C.-area defense contractor that builds tactical communications systems for the U.S. military and intelligence communities.
Your average spam email can contain a great deal of information about the systems used to blast junk email. If you’re lucky, it may even offer insight into the organization that owns the networked resources (computers, mobile devices) which have been hacked for use in sending or relaying junk messages.
Earlier this month, anti-spam activist and expert Ron Guilmette found himself poring over the “headers” for a spam message that set off a curious alert. “Headers” are the usually unseen addressing and routing details that accompany each message. They’re generally unseen because they’re hidden unless you know how and where to look for them.
Let’s take the headers from this particular email — from April 12, 2017 — as an example. To the uninitiated, email headers may seem like an overwhelming dump of information. But there really are only a few things we’re interested in here (Guilmette’s actual email address has been modified to “ronsdomain.example.com” in the otherwise unaltered spam message headers below):
Return-Path:
X-Original-To: rfg-myspace@ronsdomain.example.com
Delivered-To: rfg-myspace@ronsdomain.example.com
Received: from host.psttsxserver.com (host.tracesystems.com [72.52.186.80])
by subdomain.ronsdomain.example.com (Postfix) with ESMTP id 5FE083AE87
for ; Wed, 12 Apr 2017 13:37:44 -0700 (PDT)
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/relaxed; d=gtacs.com;
s=default; h=MIME-Version:Content-Type:Date:Message-ID:Subject:To:From:
Sender:Reply-To:Cc:Content-Transfer-Encoding:Content-ID:Content-Description:
Resent-Date:Resent-From:Resent-Sender:Resent-To:Resent-Cc:Resent-Message-ID:
In-Reply-To:References:List-Id:List-Help:List-Unsubscribe:List-Subscribe:
List-Post:List-Owner:List-Archive;
Received: from [186.226.237.238] (port=41986 helo=[127.0.0.1])by host.psttsxserver.com with esmtpsa (TLSv1:DHE-RSA-AES256-SHA:256)(Exim 4.87)(envelope-from id 1cyP1J-0004K8-OR for rfg-myspace@ronsdomain.example.com; Wed, 12 Apr 2017 16:37:42 -0400
From: dan@gtacs.com
To: rfg-myspace@ronsdomain.example.com
Subject: Discover The Secret How Movies & Pop Stars Are Still In Shape
Message-ID:
X-Priority: 3
Importance: Normal
Date: Wed, 12 Apr 2017 22:37:39 +0200
X-Original-Content-Type: multipart/alternative;
boundary=”–InfrawareEmailBoundaryDepth1_FD5E8CC5–”
MIME-Version: 1.0
X-Mailer: Infraware POLARIS Mobile Mailer v2.5
X-AntiAbuse: This header was added to track abuse, please include it with any abuse report
X-AntiAbuse: Primary Hostname – host.psttsxserver.com
X-AntiAbuse: Original Domain – ronsdomain.example.com
X-AntiAbuse: Originator/Caller UID/GID – [47 12] / [47 12]
X-AntiAbuse: Sender Address Domain – gtacs.com
X-Get-Message-Sender-Via: host.psttsxserver.com: authenticated_id: dan@gtacs.com
X-Authenticated-Sender: host.psttsxserver.com: dan@gtacs.com
Celebrities always have to look good and that’s as hard as you might
{… snipped…}
In this case, the return address is dan@gtacs.com. The other bit to notice is the Internet address and domain referenced in the fourth line, after “Received,” which reads: “from host.psttsxserver.com (host.tracesystems.com [72.52.186.80])”
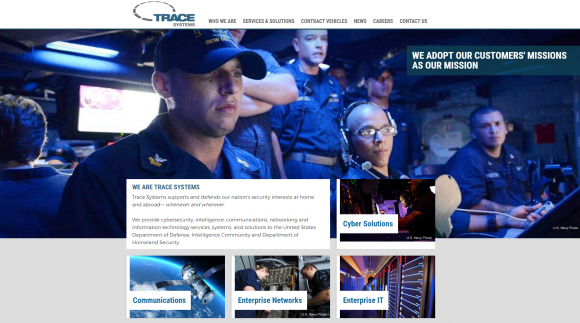
Gtacs.com belongs to the Trace Systems GTACS Team Portal, a Web site explaining that GTACS is part of the Trace Systems Team, which contracts to provide “a full range of tactical communications systems, systems engineering, integration, installation and technical support services to the Department of Defense (DoD), Department of Homeland Security (DHS), and Intelligence Community customers.” The company lists some of its customers here.
The home page of Trace Systems.
Both Gtacs.com and tracesystems.com say the companies “provide Cybersecurity and Intelligence expertise in support of national security interests: “GTACS is a contract vehicle that will be used by a variety of customers within the scope of C3T systems, equipment, services and data,” the company’s site says. The “C3T” part is military speak for “Command, Control, Communications, and Tactical.”
Passive domain name system (DNS) records maintained by Farsight Security for the Internet address listed in the spam headers — 72.52.186.80 — show that gtacs.com was at one time on that same Internet address along with many domains and subdomains associated with Trace Systems.
It is true that some of an email’s header information can be forged. For example, spammers and their tools can falsify the email address in the “from:” line of the message, as well as in the “reply-to:” portion of the missive. But neither appears to have been forged in this particular piece of pharmacy spam.