Nitin Pai
More than a trillion yuans, the restructuring of the PLA calls for a wholesale review of India’s defence structure beyond what the Kargil Review Commission advised.
In my Business Standard column I draw attention to Beijing’s bold steps to restructure the Chinese armed forces and make them capable of modern warfighting.
The conventional view is that Xi Jinping’s moves, including PLA reform, are intended to grab as much power as possible. My own take is that as far as the PLA is concerned, the reforms are primarily intended to create a force that can meet and challenge the United States in the medium term. The structural reforms are bold and politically risky, and also ensure that no PLA general is too powerful.
It is a question for our strategists, high policymakers and national leaders to assess whether India can afford to delay the structural reforms that were deemed urgent in 2002.
The Asian Balance: Look at China’s defence reforms
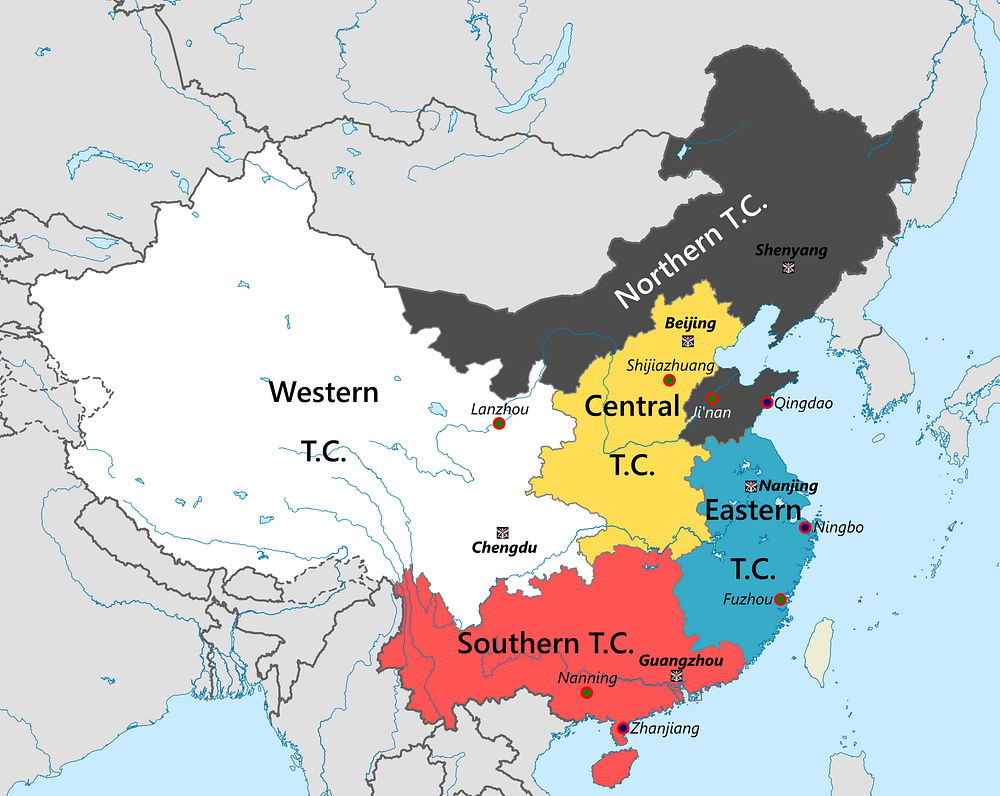 Image: Li Chao, et al/Wikimedia Commons
Image: Li Chao, et al/Wikimedia Commons
What caught public attention last week was the announcement that China’s defence outlays have crossed a trillion yuan ($151 billion) for the first time, albeit growing at a slower 7 per cent in line with slower economic growth expectations.






