David Axe
The Democrats’ cyberattackers had lots of practice
On Dec. 29, 2016, the FBI and the U.S. Department of Homeland Security’s National Cybersecurity and Communications Integration Center confirmedagain what they had initially warned about months earlier — that the Russian government hacked the 2016 U.S. presidential election.
Tampering with the election — specifically by gaining access to the Hillary Clinton campaign’s internal emails and leaking them to the U.S. media via Wikileaks and other front organizations — was simply the latest, and arguably crowning, achievement of Russia’s government-sponsored professional hackathon.
Indeed, the U.S. intelligence community’s December 2016 report on the Russian hacks listed scores of aliases that it attributes to Moscow’s cyberattackers. Tracing just one of those reveals the depth, scale and sophistication of Russia’s assault on the world’s information infrastructure.
It’s been going on for years.
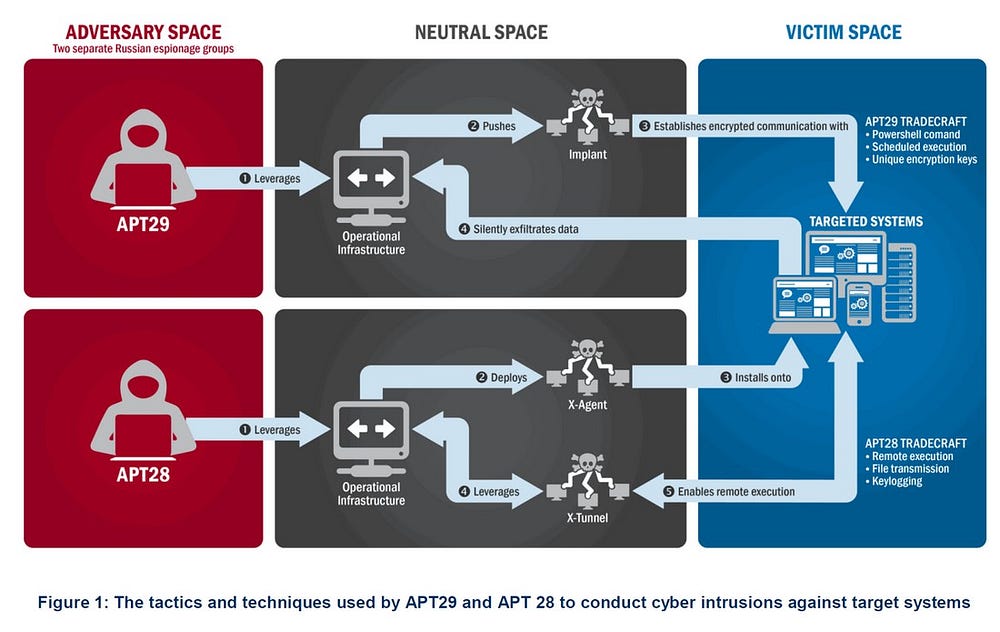
The FBI and DHS mapped out for nonspecialists how at least two Russian cyberespionage efforts, known as Advanced Persistent Threat 28 and Advanced Persistent Threat 29, tricked members of “a U.S. political party” — the Democrats — to click on malicious links and unwittingly provide access to the party’s servers.
APT28 and APT29 pilfered Democrats’ electronic communications and passed them along primarily to the notoriously anti-Clinton espionage group Wikileaks, which distributed the emails and helped to create the impression of scandal, although in fact the emails amounted to little more than typical internal business for a political party.
“This activity by [Russian intelligence services] is part of an ongoing campaign of cyber-enabled operations directed at the U.S. government and its citizens,” the FBI and DHS explained.
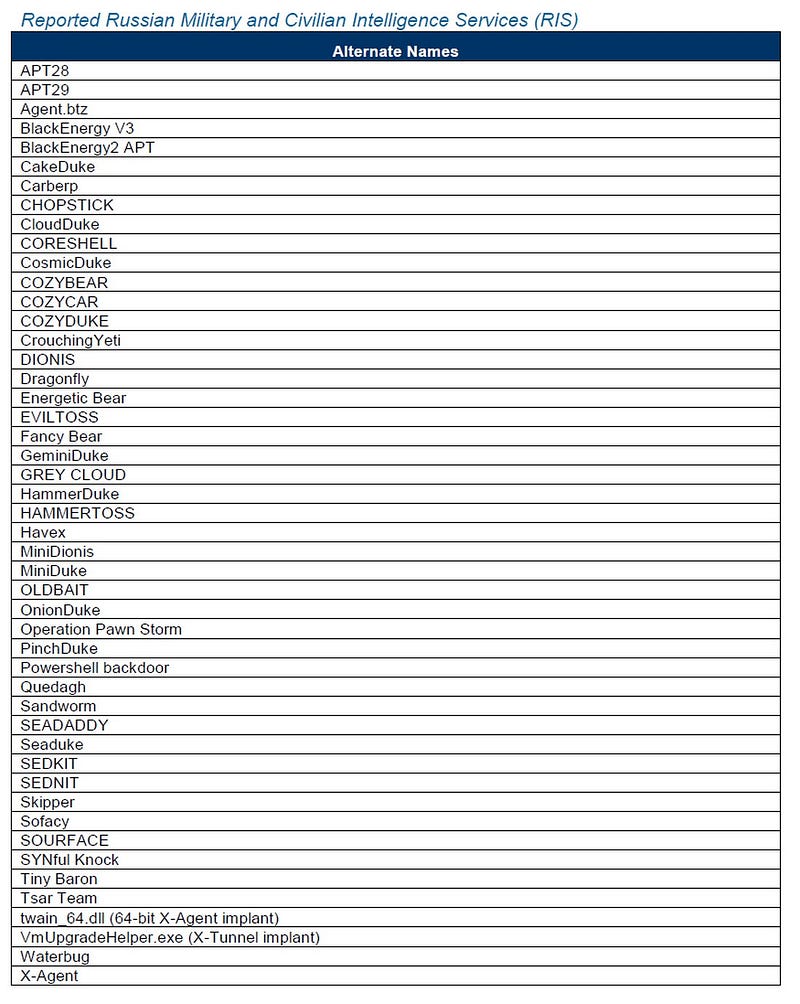
That “ongoing campaign” breaks down into no fewer than 48 identifiable hacking campaigns, which the FBI and DHS helpfully listed in their report. Just one of these campaigns, known as Crouching Yeti, first struck way back in 2010, targeting — at least at first — the power and industrial sectors of several countries, according to Russia-based cybersecurity firm Kaspersky, which is owned by a British holding company.
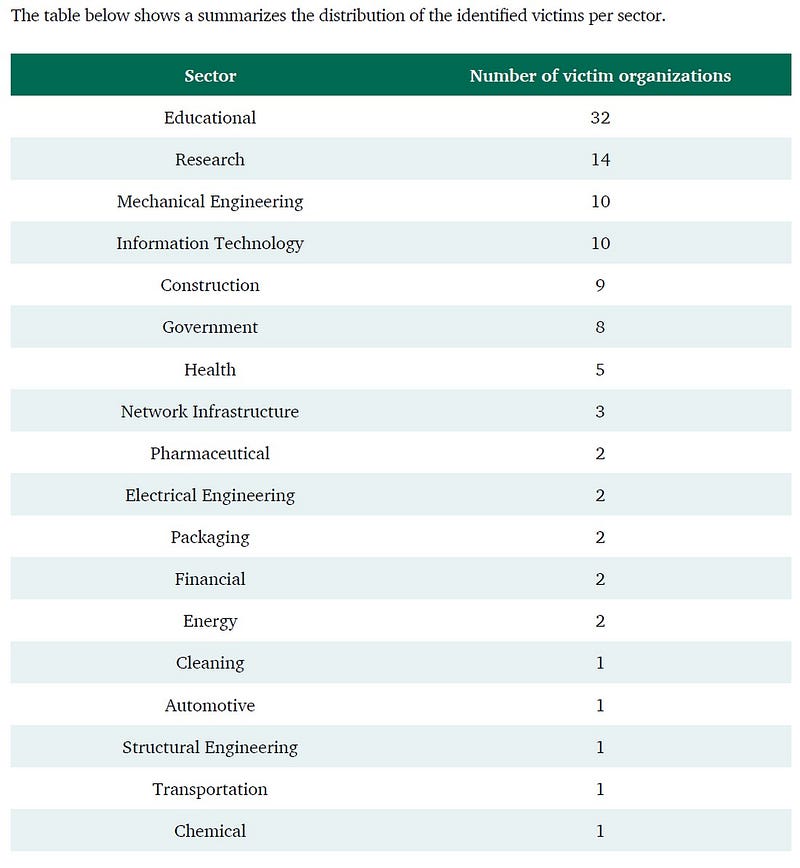
“The Crouching Yeti actor has been performing massive surveillance campaigns over the last few years, at least since 2010,” Kaspersky reported in 2014. By then, Kaspersky had counted no fewer than 2,800 separate victims of Crouching Yeti’s attacks in 99 countries — but largely concentrated in the United States and Spain.
 Kaspersky art
Kaspersky art
Over time, Kaspersky observed Crouching Yeti widening its assault to include a broader range of targets. By 2014, universities and research organizations were the main victims — with government targets not far behind.
“This victim list reinforces the interests shown by the Crouching Yeti actor in strategic targets, but also shows the interest of the group in many other not-so-obvious institutions,” Kaspersky noted. “We believe they might be collateral victims, but it might also be fair to redefine the Crouching Yeti actor not only as a highly targeted one in a very specific area of interest, but a broad surveillance campaign with interests in different sectors.”
Based on the FBI and DHS’s report, by 2016 those “different sectors” apparently included America’s presidential election. As the Russian hackers behind the Crouching Yeti cyberassault infiltrated the U.S. electoral system, they drew upon no fewer than six years of experience attacking other institutions.
In other words, Russia worked long and hard to eventually work its way into the Democrats’ servers.
No comments:
Post a Comment